Most people aren’t well-versed in the nuances of cybersecurity, so they tend to listen to, and share information that isn’t always correct. There are plenty of myths floating around about these topics. So many in fact, we felt it necessary for us to set the record straight and share our top 5 cybersecurity myths.
We’re here to make sure you ignore the “Macs can’t get viruses” rhetoric and get the correct information to keep yourself secure. Let’s dive right in.
Myth #1: MY BUSINESS ISN’T BIG ENOUGH TO NEED CYBERSECURITY
All businesses, no matter how big or small, will benefit from having cybersecurity services. It doesn’t matter if you’re a team of 5 or 500, hackers don’t discriminate. They’re looking for the easiest way to get into your computer systems and wreak havoc. Slow internet speeds, constant crashing, data corruption are all less than ideal. Having a cybersecurity professional who knows how to combat these issues are important and can save you time and money in the long run.
Check out our Deeper Dive Recording on “10 Cybersecurity Myths You Need To Be Aware Of” here.
Myth #2: MY COMPUTER IS IMMUNE TO MALWARE AND RANSOMWARE
This is a popular myth among Apple users. Unfortunately, it’s just not true. The fact is Mac’s Operating System (OS) can, and has been, infected with viruses and malware. It doesn’t happen as often as with Windows simply because there aren’t as many viruses designed to attack the Mac OS. In addition, most businesses still use Windows as their default OS. Now that you’re informed, you can take the next steps to make sure your cybersecurity efforts are up to par regardless of the OS you use.
Myth #3: HIRING AN IT PROFESSIONAL IS EXPENSIVE
While it’s true that large IT companies can cost a pretty penny to do business with, they aren’t your only option. There are many smaller, local IT companies who will work within your budget, and can perform the same services of a larger business. In fact, they may be better equipped to handle the unique needs of a small business because they are a small to medium-sized business themself.
Myth #4: MOST PEOPLE CAN EASILY SPOT A PHISHING EMAIL
This is a myth we actually wish were true. If most people had a “phishing email radar”, and could spot them all the time, hackers might not use this form of attack so often. There’s a reason it’s one of the most used attack vectors: it works. A phishing email is disguised as a regular email from a trusted company. One popular phishing scam is the email claiming to be from your bank stating there is a problem with your account, and they need your login credentials to fix it.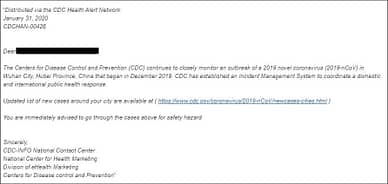
Remember, your bank will never ask you to provide your personal information through email. There are several ways you can spot phishing emails – look closely at the sender to see if the email is really from a legitimate source or look out for spelling and grammatical errors in the copy. Hackers are becoming increasingly sophisticated with phishing emails, so you need to stay vigilant.
Myth #5: I HAVE ANTIVIRUS/FIREWALL SOFTWARE, I DON’T NEED CYBERSECURITY
It’s very common to think that because you use software designed to either spot or get rid of various cyber threats, hiring a cybersecurity provider is unnecessary. The reason this is false comes down to one important thing: software is artificial intelligence; it cannot connect with you when something goes seriously wrong and it’s beyond your understanding to fix the issue. If you have a malware breach, the software can’t walk you through why it happened, nor will it give you tips to prevent it in the future. It will just find and (hopefully) destroy the malicious software in your computer.
Having a cybersecurity provider offers a much better experience. You get personalized service when it comes to security issues or breaches, and your provider should always make sure you have the best available software to prevent it in the future. They should also be willing to walk you through how the breach occurred, and how to properly respond.
Download the “5 Cybersecurity Myths – Busted!” infographic here.
As you can see, there are plenty of myths floating around about cybersecurity. Schedule your FREE 30 minute Security Assessment with us now. We will expose vulnerabilities within your organization that you can immediately use to improve your overall security stance.
