Cybersecurity Solutions
Your Clients Will Thank you
CyberSecurity Survival Kit
Our Cybersecurity Survival Kit is an industry leading cybersecurity solution. We use best of breed cyber technology to protect your organization, keep your data safe, and save your company money.
Cyber Security Services to KEep Your Business and Your Clients Protected.
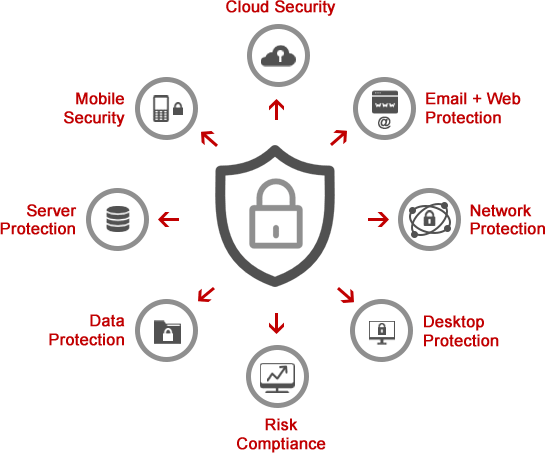
Cybersecurity Services
What We Do
Cybersecurity Services
Anti-virus programs and typical firewalls are practically useless these days. Learn how our cybersecurity solutions and technologies help companies protect their data better than ever.
CyberSecurity Training
Educational Speaking
Cyber security Services
How we Make It Possible
“Best of Breed” Products
All of the solutions we use are generally considered “best-of-breed”. As new security challenges continually arise, we constantly evaluate our product stack and add, remove, or change products.
These products have management consoles that allow us to detect and respond to threats in real-time, as well as build reports to effectively plan for future protection. We use these in our own Security Operations Center (SOC) and Network Operations Center (NOC), as well as leveraging our partner’s SOCs.
We integrate these with other monitoring and reporting tools to further raise information to responders and analysts.
Our SOC and NOC tools are hosted either on the vendors own platforms, or our own in what is “The Most Advanced Data Center on the Planet.”

Defense in Depth Principle
Defense in depth is a concept used in Information security in which multiple layers of security controls (defense) are placed throughout an information technology (IT) system. Its intent is to provide redundancy in the event a security control fails or a vulnerability is exploited. It can cover aspects of personnel, procedural, technical and physical security for the duration of the system’s life cycle. When envisioned as an onion, each layer creates redundancies in case of failure, defeat, or bypass. The core of the onion is the asset being protected. Defense in Depth can be divided into 3 controls.
Physical Controls
Physical controls are things like fences, video surveillance, and locked doors.
Technical Controls
Some examples include EDRs, fingerprint readers, multi-factor authentication, DNS filtering, etc.
Administrative Controls
Examples of Layers
Using more than one of the following is properly incorporating Defense in Depth:
- Encryption
- Hashing passwords
- Logging and auditing
- Security Information and Event Management tool (SIEM)
- Multi-factor authentication
- Vulnerability scanners
- Timed access control
- Internet Security Awareness Training
- Sandboxing
- Intrusion detection systems (IDS)
- Firewalls (hardware or software)
- Demilitarized zones (DMZ)
- Intrusion Protection SystemsVirtual private network (VPN)
- Biometrics
- Data-centric security
- Physical security (e.g. deadbolt locks)
- Backups
- Virtualization
- Incident Response
- Password Management
- Enterprise Email
- Encrypted Email
- Spamfiltering
- Managed Website Hosting
- VPN
- Remote Access
- DNS filtering
- IT Management
- Patch Management
- SIEM
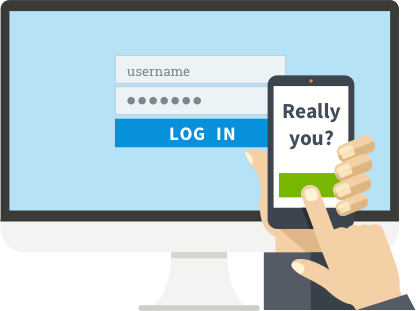
Two Factor Authentication
One of the most important things to add to any authentication method is 2 Factor Authentication (2FA), or Multi-Factor Authenticatoin (MFA). If you’ve used a third number besides username and password with a site like your bank, then you have used MFA before.
The 3rd “code” is typically a hardware device that you press a button on, a text message or app pop-up on your phone. These codes are time-sensitive, and will not work after a period of time usually no more than 5 minutes.
Without this time-sensitive number or code, even if someone has your username and password, they cannot access your account. You should use MFA wherever and whenever possible.
Our MFA solution is compatible with Google Authenticator and is stored securely, ready for you to use across all your devices: computer, tablet, phone, and even smart watch.
With compatible devices, the MFA can even “push” a notification to your phone or smart watch and you can quickly log into your PC remotely or other secure destination by just pressing a button, which makes it extremely easy to use ,while at the same time, dramatically increasing your personal and utility security.

DNS Security
DNS security protects your computers and network from malicious websites, phishing and botnet attacks, and ransomware.
It works by intercepting all outgoing traffic on your network and comparing it to known malicious sites and servers. Interestingly, many types of ransomware has to “phone home” before encrypting the files, so if the “home” server is known to be a ransomware server, DNS Security will block the request, effectively shutting down the attack.

Password Management
The BEST way to manage your security credentials is with a good password manager. Used properly, not only can you create unique sets of credentials for every website or application you use, you don’t even have to care what the password is, or even type it in.
This means that you can use 20 randomly generated characters for a password instead of a word (which is vulnerable to dictionary attacks, and yes, hacker dictionaries include leet speak like “3v3n” instead of “even”.
Endpoint Protection
Off-the-shelf antivirus (AV) products are pretty much useless with the modern technologies that hackers use today, especially since the NSA leak.
Traditional AV looks for known code “signatures” to detect viruses, but many modern attacks use polymorphic technologies to scramble any signature. Furthermore, it sometimes takes months for a particular virus signature to be added to an AV. That is not good enough.
With our Endpoint Detection & Response (EDR), the network and computers are monitored for behavior characteristics and use machine learning and artificial intelligence to detect virus attacks even before they have been detected in the wild. EDR software is particularly effective in stopping ransomware attacks, because these attacks don’t even use a “virus” (that’s why AV is pretty much useless these days).
SIEM

VPN
VPN stands for Virtual Private Network. A VPN protects field offices and SCADA device communication over the Internet by wrapping all data flow inside an encrypted wrapper. This means even if someone sees the actual traffic on the internet, it is impossible to tell what it is, much less what is in the data packets.
Safe Backups
Backups should be automatic, off-site, and monitored. Backups that are done to another drive on the network, or to a USB drive are not secure from ransomware attacks. They also will be destroyed in case of a catastrophic facility loss, or lost if you take it off premises.
What Does all This Mean?
Our Clients Can Sleep Soundly
We are confident in their up-to-date knowledge in the ever-changing technology world.
"IronTech Security keeps our information secure, solves any IT issue quickly and efficiently, and provides specific, customized solutions. The single biggest benefit to our company since moving to IronTech is the knowledge that our information is secure and if we encounter any technology issues, they can address and find solutions quickly and efficiently. As a local business, they know our company and our needs and are able to make specific recommendations and customize solutions. They’re able to provide in-office, same-day assistance, and they stay up-to-date with the ever changing technology world.”
Irontech Security provides peace of mind that we’re backed up and secure every night.
"The biggest benefit of working with IronTech Security is knowing that everything is being backed up every night. Calling for help is easy, and I’ve been happy with the experience and results. Undecided about choosing a service? I may not know anything about your other choices, but I’d recommend that you go with IronTech Security.”
IRONTECH PROVIDES TOP-TIER IT SERVICE WITH THE BENEFIT OF THE ENTIRE COMPANY’S “INSTITUTIONAL KNOWLEDGE” RAPID RESPONSE, UPDATES AND SERVICE. 100% BENEFIT TO MY LAW FIRM.
“I get top-tier IT service with the benefit of the entire company’s “institutional knowledge” for a price that is a fraction of what it would cost me to have just a SINGLE dedicated IT person on staff. IronTech responds rapidly to my issues and concerns and updates me via emails every time anything is done on a given work ticket. They provide a valuable interface between my firm and our ISP for phone service. I’ve hired other IT providers before, but no other provider can compare with the level of service and knowledge I get from IronTech.”
