Press Release
For Immediate Release: July 28, 2021
Contact:
Kindsey Haynes, Marketing Director
IronTech Security
479.434.1400
irontechsecurity.com
kindsey.haynes@irontechsecurity.com
How Long Does It Take a Hacker to Brute Force a Password?
Fort Smith, Ark. – According to leading cybersecurity company, IronTech Security, brute force is one tactic hackers use to access a system. Brute force attacks refer to the many methods of hacking that all involve guessing passwords in order. If a password is only four or five characters (whether they are just numbers or a combination of numbers, letters and symbols), there’s a very high chance that it will be hacked instantly. However, if a password is only numbers and up to 18 characters, it could take a hacker up to nine months to crack the code.
Consider that at least 60% of people reuse passwords across multiple sites; an estimated 81% of data breaches are due to poor password hygiene; and although 91% of participants in a recent survey understand the risk of password reuse, 59% admitted doing it anyway. Most people will choose passwords that can be divided into 24 common combinations, and 49% of users will only change one letter or digit in one of their preferred passwords when required to make a new password. Based on an analysis of the data from Dark Web ID, the most categories of information used to generate bad passwords in 2020 were names, sports, food, places, animals, and famous people/characters.
Most brute force attacks employ some sort of automation which allows almost limitless quantities of passwords to be fed into a system. A simple example of a brute force attack is a hacker simply guessing a person’s password based on relevant clues. However, most are more sophisticated. Credential recycling, for example, is predicated on the fact that many people reuse passwords, some of which will have been exposed by previous data breaches. Reverse brute force attacks involve hackers taking some of the most commonly used passwords and attempting to guess associated user names.
The longer, more complex and unique a password is, the less likely it is to fall victim to a password attack. This graphic shows how long it would take a hacker to crack a password.
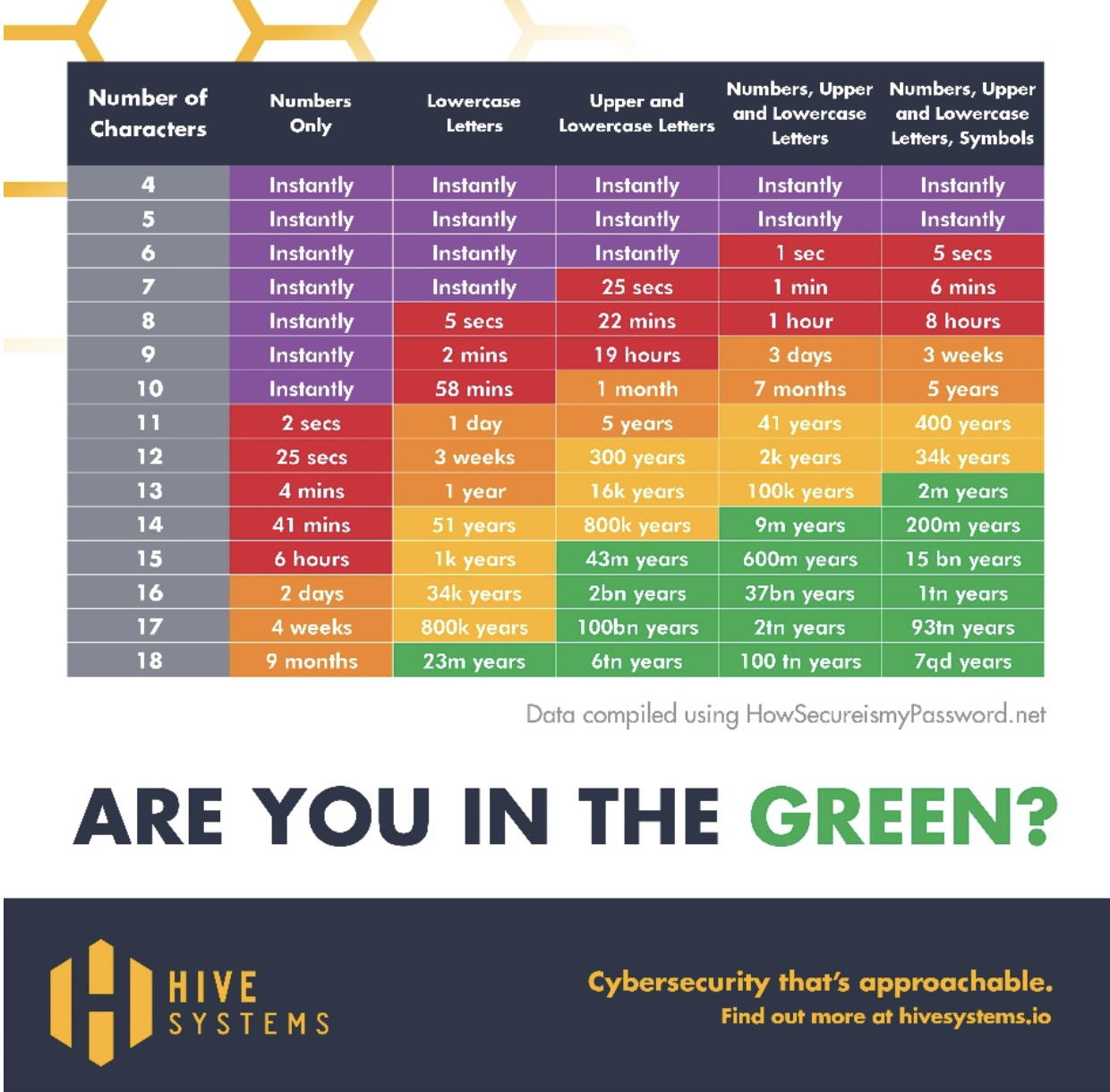
“We recommend everyone use a password manager,” says IronTech Security CEO Tom Kirkham. “Not only is it easy, it is convenient because it creates and stores passwords for the user. All that user needs to do is remember one master password to gain access to all credentials.”
A password manager is essentially an encrypted digital vault that stores secure password login information used to access apps and accounts on a mobile device, websites, and other services. In addition to keeping identity, credentials and sensitive data safe, the best password manager also has a password generator to create strong, unique passwords and ensure the same password is not used in multiple places.
Kirkham says there are many free password managers, but that the paid versions still only cost from about $30 to $60 a year.
For more information contact Kindsey Haynes at kindsey.haynes@irontechsecurity.com or visit www.irontechsecurity.com.
IronTech Security, is a leading managed security service provider (MSSP), delivering exceptional IT and cybersecurity services to water utilities. From network security to strengthening employee security, IronTech Security offers a number of solutions to financial and legal organizations, manufacturers and water utilities, to name a few, that need to protect their organization and their customers’ data. Providing unmatched security, support and services, IronTech Security is proud to give clients peace-of-mind, allowing them to focus on their goals and success. Watch for Tom Kirkham’s new book: The Cyber Pandemic Survival Guide – Protecting Yourself From The Coming Worldwide Cyber War.
For more information on how long it takes for a hacker to brute force a password, download our free checklist for your business with 15 Ways To Protect Your Business from a Cyberattack

