Many believe information security is information technology, and their IT guy handles all of their cybersecurity. This is a common misconception. Information technology specializes in technology, not security. This post will discuss the difference between information technology and information security.
What is the difference between information technology and information security?
Information security and information technology both have different principles and objectives. Information security, sometimes shortened to infosec, refers to the processes and methodologies which are designed and implemented to protect print, electronic, or any other form of confidential, private and sensitive information or data from unauthorized access, use, misuse, disclosure, destruction, modification, or disruption. Information Technology is the study or use of systems (computers and telecommunications) for storing, retrieving, and sending information. Cybersecurity is not a specialization or subset of information technology; it is its own specialty. As one of the best cyber security companies in the industry today, we take the speciality very seriously.
Below, are some examples of the different job duties between Information Technology and Information Security.
Information Technology Goals:
CIO (Your IT Guy, MSP)
MSP- Managed Services Provider
- Help Desk
- Network Management
- Desktop Management
- Patch Management
- Productivity
- Server Procurement, Deployment & Management
- Runs as Efficiently as Possible
Information Security Goals:
Virtual CISO (IronTech Security, MSSP)
MSSP- Managed Security Services Provider
- Security Awareness Training
- Intrusion Detection/Prevention
- Security Response
- Disaster Recovery/Continuity Management
- Privacy
- Identity & Access Management
- Investigations and Forensics
As you can see, there is a big difference between the roles of information technology and information security. It is critical that you have someone in the role of an MSP and someone in the role of an MSSP for your organization.
Just like there are specialties in information technology, there are in information security as well.
- Red Blue Team Specialists
- Penetration Testers
- SOC Admins
- Risk Analysis
- Business Community
- Backup Specialty
- Administrative Control Creation
Conflict of Interest
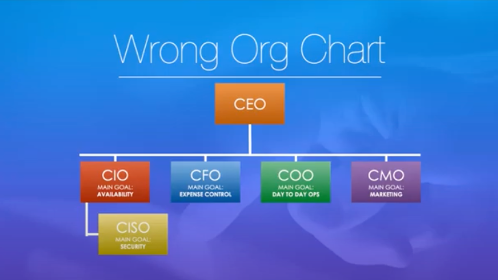
There is a major conflict of interest between the CISO and CIO. CISOs should not be reporting to the IT department or CIO, but to the CEO. The CISOs main goal is security, the CIOs main goal is to keep the network up and running. 25% of IT workers say they don’t enforce security policies universally and 4% don’t enforce those policies at all due to the hassle involved with managing policies to concerns over workforce productivity.
Conflict of interest occurs because the CISO may need to patch a software update, but the CIO or other roles are worried about computer crashes, yet the patch needs to be made ASAP. That decision needs to be made by the CEO not the CIO.
Here are some other examples of conflict of interest:
CFO – Cybersecurity Costs Too Much
COO– Security Hurts Productivity
CMO – Everyone Should Have Access to Customer Data
CIO – Network Cannot go Down
Below, is the incorrect org chart, and the one that most people tend to follow.
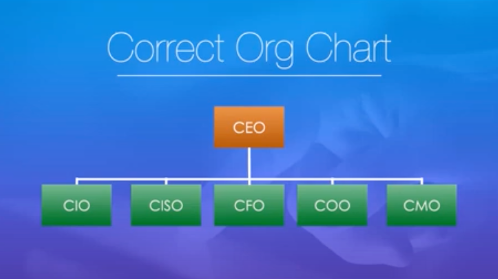
Below, is the correct org chart. This org chart has every role reporting to the CEO. The CISO is not reporting to the CIO, just to the CEO.
Cybersecurity at the CEO Level
Information Security is about existential business risk, not IT risk. That risk is growing everyday as malicious actors become more advanced. Information security is important to any business, bottom line, and should be taken serious at every level of the organization. CEOs need to take action and ensure their organization is not left vulnerable.
IronTech Security works directly with your IT staff or MSP to ensure you have the utmost protection. You could consider us your virtual CISO. We don’t replace your IT team, we only make them better.
Schedule a security assessment with us here, invite your IT guy, and let’s sit down to see where your organization is left vulnerable. You both will walk away from the meeting knowing exactly how to strengthen your security stance. Hopefully this post gives you a much better understanding of the difference between information technology and information security, and why information security vs information technology is so important.
Check out our Deeper Dive: Quick Look Series recording on “Cybersecurity Overview for IT Professionals” here.
