The NIST Cybersecurity Framework provides guidance on how organizations can assess and improve their ability to prevent, detect, and respond to cyber-attacks. A well-designed security stack consists of layers including systems, tools, and polices. These tools need to be implemented to cover each NIST layer in at least one way. The NIST Cybersecurity Framework helps organizations in expressing their management of cybersecurity. This is very similar to our layered security approach.The idea behind layered security is that you create multiple security layers that resist attacks rather than a single-solution approach that leaves loopholes. A single-solution approach is not reliable and can leave your network vulnerable to further attacks. Layered security is also known as defense in depth. Following the NIST Cybersecurity Framework will help your organization in expressing cybersecurity risk by organizing information, enabling risk management decisions, addressing threats, and improving by learning from previous activities. As well, the implementation of the NIST Cybersecurity Framework will show you the impact of investment made in cybersecurity. Investments in planning and exercises result in a reduced number of threats and vulnerabilities.
We compare the layers of the NIST Cybersecurity Framework to the layers of an onion, each layer critical to protecting the assets within.
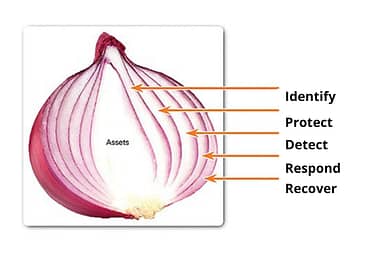 Identify: Identify risks and risk management within your organization. Understand your employees and your organizations security maturity to see where your organization stands. This helps you manage risks to systems, people and assets. Identify and control who has access to your valuable data and information. Identify a risk management strategy for your organization and create cybersecurity policies and procedures.
Identify: Identify risks and risk management within your organization. Understand your employees and your organizations security maturity to see where your organization stands. This helps you manage risks to systems, people and assets. Identify and control who has access to your valuable data and information. Identify a risk management strategy for your organization and create cybersecurity policies and procedures.
Protect: Identify management and access control. The protection layer supports the ability to limit or contain the impact of a potential cybersecurity event. Assure you have protective technology in place, as well as data and information security. Protect your organization by implementing a continuous cybersecurity awareness training. It is critical that employees are aware of current threats and risks held by your organization. Cyber criminals are becoming more advanced every single day leaving one-and-done trainings inadequate.
Detect: Continuously monitor for security events and anomalies. Make sure your organization has the appropriate security in place to detect any red flags within your network and system. Implement continuous security monitoring capabilities to monitor for events. Cybersecurity threats occur on a daily basis, it is essential that your organization detects a threat as soon as it occurs.
Respond: Contain and mitigate security events. The respond layer supports the ability to contain the impact of a potential cybersecurity incident. Develop a plan for disasters and information security incidents before they happen. Consider the immediate actions you and your employees will need to take in case of a cyber-attack. Analyze the effectiveness of response activities.
Recover: Plan for your next breach and know how you will recover. Have a business continuity plan in place. Make improvements in your processes, procedures, and technologies to improve your security posture. The recover layer supports timely recovery to normal operations to reduce the impact from a cybersecurity incident. This includes ensuring recovery processes and procedures and implementing improvements based on lessons learned. As you can see, the implementation of the NIST Cybersecurity Framework will make your organization dramatically less vulnerable to threats and attacks. It is critical to have security layers in place; this approach will create a solution that will resist attacks unlike a single-solution approach. Single-solution approaches are not reliable and will leave your organization vulnerable to cyber-attacks. Assure you and your employees are knowledgeable of all current risks and threats held by your organization. Check out this infographic on the NIST Cybersecurity Framework.

Benefits of NIST CSF
Implementing NIST CSF into any organization can be a positive change and can help keep malicious cyber threats at bay. With NIST CSF the organization is constantly performing risk analysis and risk management tasks. These allow for the most accurate information regarding the health-posture of the systems and indicate to the organization any urgent matters or vulnerabilities that need to be addressed. The five-step lifecycle process allows for a long-term cybersecurity and risk management program rather than a one-time assessment snap-shot.
The NIST framework allows for the whole organization to be involved due to cybersecurity and awareness training and risk management procedures. This begins shifting the cybersecurity culture and mindset within the organization to a more positive direction. Employees are more likely to recognize vulnerabilities and cyber threats and report them to the proper personnel in a timely manner.
Any cybersecurity framework allows for the business to build trust with potential clients and returning customers. Those that work directly with the business can feel safe knowing that the data shared is safe, protected, and up to FISMA standards.
Overall NIST CSF provides layers of protection and cyber defense. The program can be tailored to meet the goals and mission needs of the organization while still ensuring the confidentiality, integrity, and availability of data located within the organizational boundaries remains intact.
In Summary – Understanding the NIST Cybersecurity Framework
Cybersecurity is a continuous lifecycle. There is no right or wrong answer to what type of cybersecurity framework is implemented and what standards an organization chooses to follow. As vulnerabilities and malicious cyber attacks become more prevalent and complex overtime, the need for multiple layers of cyber protection is crucial. The different controls that NIST frameworks suggest implementing can harden critical infrastructure and make it difficult for malicious cyber actors to penetrate the system and gain valuable data. NIST CSF allows for constant review and evaluation of the network. Due to this, the organization will always have a strong idea of the current health-posture of the network.
Download an infographic on The NIST CSF here!
Contact us today for a FREE Security & Risk Assessment. We will uncover where your business is vulnerable to cyber attacks.
479-434-1400
